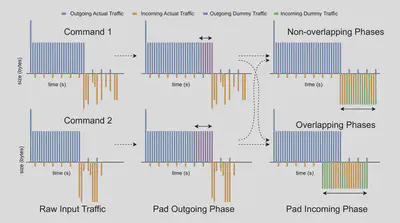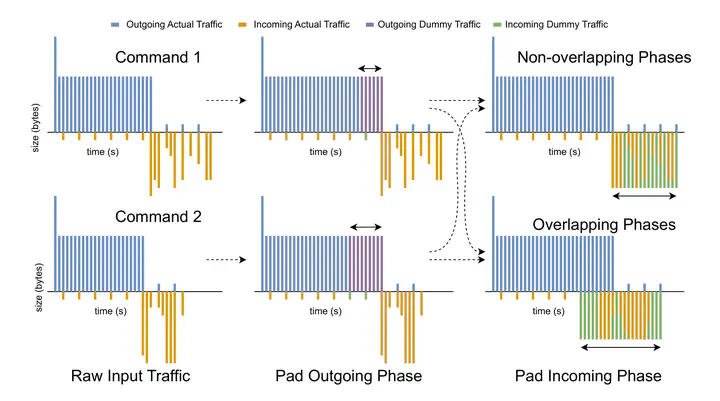
Abstract
Voice assistants have become ubiquitous, yet they remain vulnerable to network traffic fingerprinting attacks that can expose sensitive user information. Existing defenses either impose high overheads or fail against advanced attacks. This paper addresses these issues by introducing and evaluating PriVA-C, a fingerprinting defense mechanism tailored specifically for voice assistants. Unlike prior approaches that treat voice assistant traffic as generic web traffic, we analyze its unique characteristics to design a more effective defense. Our approach prioritizes limiting information leakage rather than targeting specific attack vectors, achieving a significant reduction in attacker accuracy from 89% to 13%. We also propose a more practically deployable version of our defense, which protects only traffic directed to the primary voice assistant domain, reducing attacker accuracy to 19%. We implement a functional prototype using the Alexa SDK, conduct user testing, and assess its performance using real network traffic. Our results demonstrate that our proposed defense effectively mitigates fingerprinting attacks while maintaining low overhead and preserving the user experience